CYBER PRUDENCE
Mr. K. I. Pavan Kumar
INTRODUCTION:
A disciple asked his Sage "what is cause and effect" Sage
reacted aggressively and slapped on disciple’s face. The wounded disciple kept quite.
After some time, seeing the wound of his disciple, Sage asked the disciple to "show
the slap". Then disciple pointed at his wound, sage said that, the wound is the
result of his slap and that is not the slap itself. Disciple then understood slap is the
cause and wound is the effect.
Before any sagacious man slaps on us better we understand the
relationship between ‘cyberspace’ and ‘information technology’. The
fundamental question to be clarified is whether technological advancement has created
cyberspace or discovered cyberspace? As most of the technologists believe that cyberspace
is space comprising of computers, telecommunications, software and data in a more abstract
form and as they do not attribute any significant character to the ‘space’
perhaps, they believe that cyberspace is created by the technology.
On the other hand Sociologists believe that cyberspace already exists
it is not created by technology perhaps the technological innovations might have
facilitated us in capturing or utilizing the cyberspace (though not entirety). It cannot
be said that at the early days of technological innovations there was ‘a less
cyberspace’ and now these is a ‘larger cyberspace’ because of the
technological advancement. If this is true one may be interested in evaluating the
increase of cyberspace in proportionate to the technology advancement and come up with a
mathematical formula, which is absurd.
As is pointed out no technological advancement made so far in human
history could create a separate platform for the operation of law then how come this
Information technology influencing law? Is information technology so powerful that it
redefines the legal systems itself? The answer is ‘NO’ Information technology is
not powerful in redefining the legal systems, but law is sensitive. It cannot leave any
segment of society susceptible to malicious intruders; it cannot leave any factor
influencing the human behavior uncontrolled. Cyberspace no doubt has vital influential
power over individuals because; cyberspace is nothing but an extension of the idea of
virtual reality. It should be viewed as an extension of human experience having at the
core of it the matrix or the Net.
We get annoyed if we receive unsolicited mail offering money without
work, we get disturbed when we see pornographic pictures downloading unexpectedly. We get
irritated when our mailbox is full of unnecessary material. This indicates that the
existence of the space in its generic cense (geographic) though in question it does exists
in our emotional fields.
"The Net… joins all of the computers and telephones on Earth.
It is formed by radio, telephone and cellular links with microwave transmitters beaming
information into orbit and beyond. In the 20th century, the Net was only accessible via a
computer terminal, using a device called a modem to send and receive information. But in
2013, the Net can be entered directly using your own brain, neural plugs and complex
interface programs that turn computer data into perceptual events".
Therefore, it is clear that ‘cyberspace’ is an extension of
‘human experiences’, which is with in the gamut of Law.
Many names have been developed to describe this growing area: the Net,
the World Wide Web, the Cloud, the Matrix, the Metaverse, the Datasphere, the Electronic
Frontier, and the Information Superhighway. With the increasing development of this
virtual area cyberspace is becoming a way of life. Although cyberspace also referred
as the Internet both should not be intermixed. One is instrument to access the other. The
path and destination should not be equated.
Dewitt, defines cyberspace by using William Gibson’s view, which
describes cyberspace as an imaginary realm where computer information resides.
Gibson’s definition of cyberspace sets into the reader’s mind as a
science-fiction fantasy. Latter Dewitt describes cyber space as "today’s
increasingly interconnected computer system" he maintains that cyberspace is pure
genius because what was once an imagined thing of a writer has become a reality.
There is also a view that as law believes in boundaries, any place
which does not posses boundaries would not fall with the gamut of legal jurisprudence,
As Karnow has said "it is in this digital soup, this is hyper relational environment,
that we see the death of the barrier… what we do have is, the network and the death
of dichotomy. This is fatal for the legal system, which depends, for its very life, on the
existence of barriers – after all, that’s what the law does: it utters the line
between this and that, and punishes the transgressor."… by E. A. Karnowbut
the more pertinent thing in legal studies is it should deal with persons than the place.
Law and Jurisprudence:
As we are talking about Cyber jurisprudence it is pertinent to note
the inter-relation ship between law and jurisprudence. To explain the term law, if I use
my classroom example that would be easier to understand.
Law is like a black dot on a white cardboard (picture –2.1)
The black dot can be interpreted in an innumerable number of ways.
one may call it a ‘circle’, the other may call it a
‘stigma’ on |
 picture–2.1 picture–2.1
|
Similarly the term ‘law’ may be interpreted in many ways
like, one may feel law as command of sovereign (Austin’s School of law), other
may feel that as, it emerged from the customs, it should be flexible for the common
usage The other perception is law is rightness (Ethics) of will, and this can never
be enforced by external legislation. But must be the free choice of the individual. The
others say that law is the science of the totality of the rules for which an external
legislation is possible’ (Nomology). By reading this paragraph one should not
jump to hasty conclusions like, law is vague and unscientific etc but instead, one should
keep in mind that law is a ‘perceptual science’. To put it in other way a
notion, which has majority approval, would emerge as a ‘principle’ and set of
such principles would thus form Jurisprudence. Therefore, jurisprudence is nothing but set
of majority accepted principles of a given society. This analogy is proved in the case how
jus civil and the jus gentium were merged into the broad stream of Roman
law, destined to fertilize all the legal systems of the world
Is Internet a vanishing point of law!
Law cannot function in vacuum it seeks a definite place and people
voluntarily abiding to it. If law requires some place to be operated and few individuals
consciously abiding to it, then what is the need for recognizing group of individuals as
society? And what is the need for making separate rules for their governance? Above all,
what makes a group of individuals as society? Is it mere physical existence or is their
any other thing that substantiates the matter? The need for resolving these questions has
come when we are using the term "cyber society" and thinking about its nature.
The technological inventions made so far have created and developed
"products" whereas information technology has facilitated "processes"
like process of buying, communicating, sharing ideas so an and so forth. This technology
enables people to meet, talk and live in cyberspace in the ways not possible in the real
space. The cyberspace is more intimate, accurate and unceremonious. The internet as a
medium of communication has grown exponentially with the high participation of individuals
facilitating each other with mailing, shopping, sharing online news etc. The ability of
online users to interact in sophisticated ways form "virtual communities".
The term ‘cyber society’ or ‘cyber community’ is
used very insecurely by lawyers and research scholars to refer internet users. But to
refer a group of individuals as society or community apart from many other commonalities,
the interest (proprietary and personal) of the subjects over the field of operation should
also be similar though not identical. Perhaps the reason for the tossing of the coin
"cyber society" "cyber community" by the social thinkers is its
accessibility to every individual. And this very accessibility paved the way for sharing
of ideas, moods and for building of common interests and consensus. Now law has to be
built on the premise of this consensus itself.
Law has to identify the common principles on which the cyber society is
working, what norms are governing them? And what customary practices are followed in cyber
space? Etc and out of such commonalities like customary practices, cultures, usages and
the basic norms, law has to formulated. In the words of Savigny " Law grows with the
growth and strengthens with the strength of the people and its standard of excellence will
generally be found at any given period to be in complete harmony with the prevailing ideas
of the best class of citizens". If this ‘prudence’, is not shown by the
subjects of law (netizens/citizens) then such society will be put to nullity. This
nurturing of society, whether virtual or physical, is the job of jurisprudence. Therefore
every society has to know the philosophy of law governing it and abide to that. As far as
physical society is concerned the jurists like Sir John Austin, Salmond, Sir Frederick
Pollock etc have evolved many schools of thoughts and gave possible propositions to the
jurisprudence, but for cyber society, jurisprudence is not yet formulated and is still in
the realms of legal academia. But contrary to this the ‘cyber society’ is more
of a reality today than it was ever before. On the one hand the Internet has a stake in
the economies of the world while on the other it has gripped popular imagination by
providing easy communication, entertainment, leisure and relaxation. The Internet is
continually changing the dynamics of the world. The law needs to be alive to this change
in society. Roscoe Pound once said, "Legal order must be flexible as well as stable.
Law must be overhauled continuously and refitted continually to the change in social life
which it is to govern". With that goal in mind, the Indian Parliament went about
legislating the first cyber law and christened it the Information and Technology Act,
2000.
The Need of Law in Cyber Society
The purpose of law is in the conflict itself. Where there is no dispute
or confrontation of interests there the need for law is nil. And "Conflicts arise
when there is some thing to share" more so when the shared object is scarce. This is
as much true of the family or neighborhood as the "Cyber Space". When conflicts
arise in Cyber Space, we need "Cyber Laws" to restore order to the society. When
we are discussing the emerging field of "Cyber Laws" we need therefore try to
understand how and why conflicts arise in the "Cyber World". If the conflicts in
cyberspace are not making any substantial difference with the conflicts of physical space
then the already existing laws, which are governing the physical space, are highly
sufficient to regulate cyber space as well, we need not to go for codification of a
separate legislation and for evolving new principles, but the disputes in physical space
and the disputes in virtual space are entirely different in nature. Not to go in detail
the matters of Jurisdiction, Proprietorship, liabilities of intermittent parties like ISPs
(Internet Service Providers), the doctrine of choice of law, principles of defamation, are
all put to scrutiny. To put it more understandably the reason for a separate law is
"Law" being a "Code of Conduct declared as the most suitable for a given
society", law need to make itself suitable as society changes.
This analogy can be extended to the "Cyber Society" as well.
The reason for realizing the need for cyber laws even before cyberspace takes its shape,
perhaps, is because of claiming non-cyber rights as cyber rights. As long as the trademark
owners were away from the Internet world, there were no domain name disputes. This chaotic
period of time would churn fundamental principles of cyber law and lead to the evolution
of cyber jurisprudence. We should see that there should not be conflict or overlapping
between rights of cyber society and non-cyber society. For instance, the doctrine of
adverse position has no role to play in cyber space. Because of this divergent issues
involved unless we come up with sound principles of jurisprudence applicable in cyber
space even law cannot control the cyber space entirety.
Cyber Etiquettes are not antiquities:
The role of ethics or etiquettes in cyber realm are very high more particularly when
cyber space is unorganized, checks and balances over the cyber activities are not at
standardized and where cyber crime investigating institutions are not established. The
alternative to curb the immorality is, ‘regulating oneself’.
Unlike in physical space, the regulation of individual behavior in
cyberspace is nearer to impossible unless, the governed is ethically sound. Ellickson
identifies five "controllers" that can provide substantive rules governing an
individuals behavior (see picture- 4.2)
Controller |
Substantive Rules |
Sanctions |
The actor him/herself |
Personal ethics |
Self-sanction |
Second party controllers. i.e.
the person acted upon. |
Contractual provisions |
Various self-help mechanisms |
Non-hierarchically organized
social forces |
Social norms |
Social sanctions |
Hierarchically organized
non-governmental organizations |
Organization rules |
Organization sanctions |
Governments |
Law |
State enforcement, coercive
sanctions. |
(Picture- 4.2)
Though all the controllers are equally important at their respective
level of control, personal control is more suited to the present context. What we call
"cyberspace" can be characterized as a multitude of individual.
As Oliver Williamson rightly points out about "legal
centralism"(a theory focus on alternative sets of substantive laws-with an eye
towards determining which set is optimal in terms of some pre-defined criterion such as
aggregate welfare) this is more appropriate model especially when some law making body is
in a position to choose the optimal set of laws or when people are in search of an
appropriate body to regulate there conduct. At present ‘ethical centralism’ is
needed.
It is agreed that we cannot construct watertight compartments for
ethics. At the same time we do not want to be skeptical about the role of ethics in
regulating cyber society. Because every theory evolved in regulation of ‘real
society’ has its roots in ethics, even the mostly accepted and contemporarily suited
theory of Austin’s positive law applies against those who has an etiquette of
respecting the sovereign and accepting code of conduct prescribed by him as
‘command’ and succumbs his head before executors in case of breach of the
command.
Ronald Dworkin, scholar, philosopher and educator of present day do
believe in the right to moral independence. He empathically maintains that people have a
right to access those things that they think will make them happy. Others have no right to
stop them from gaining these things just because these other people do not approve of how
they want to live their lives. More interestingly, he opines that, the prescribed ideology
behind making law is not just reporting common consensus or to function like a tool to
achieve society’s policy goals but rather Dworkin proposes law to be ethical.
Therefore, the ethical issues are still relevant even we are proceeding towards more
technical and technological life.
Approach of law:
A fundamental theme running through most cyberpunk literature is that
(in the near future Earth) commodities are unimportant. Since anything can be
manufactured, very cheaply, manufactured goods (and the commodities that are needed to
create them) are no longer central to economic life. The only real commodity is
information. With information so fundamental to the business world, the mechanics of
business are vastly different from those we know at present. In our current product and
service based business world, we are used to dealing with items that can be stamped,
traced, taxed, counted and measured. When the primary commodity is information, these
attributes no longer apply and the structure of the business world is different. Many
people have already recognized this,
It is an admitted fact that one or the other devise, whether
ethical (self) or institutional, is needed to regulate any activity carried on in cyber
space, but interestingly, one important point is missing from our analysis that is what to
regulate? Is it flow of information or is it the place where information is flowing? Or is
it the subjects (individuals) who are accessing the information to be regulated? If it
is the place, where information is flowing, to be regulated then invariably law has to
attribute some significant legal status to the cyber space and accordingly it has to
deliberate upon the character, nature, jurisdiction and functions of the cyber space.
If the subject matter of law are the individuals, as they be in
physical space using physical devises itself, already existing laws are suffice to
clampdown misuse of IT and to curb technological mal practices. We need not to search
terminologies to name the crime committed as well no need of establishing new institutions
like cyber police station, cyber cops etc. But the difficulty in this approach is, at
times it becomes impossible to trace out individual behind a crime committed and it is
impracticable to expect that every cyber offence originate from physical space.
If it is the ‘information’, which is subjected to the
regulation by the law then the horizons of the IT law should be so expended that it deal
with production, distribution, dissemination, processing of information as a whole as most
of the Communication Acts does in the resent past, like German Information and
Communication Services Act (1998) and British White Paper, Proposing the creation of a
Cross-media regulatory authority, published in the year 2000 and similarly The Indian
Communications Convergence Bill 2000 which does not attribute much difference between the
e-mail viewed in television and laptop. This approach of law wither away the concept of
cyber crime, cyber theft so on and so forth and perhaps may swab lot of confusion about
Information space and help us in understanding the nature of cyber activities. But
difficulty in equating laws of information technology with communication regulations
primarily is the communications regulations deal information more or less as a
‘product’ where as the information technology is a process. Overlooking of this
significant difference may pose serious problems.
Theories on Information Law approach:
From the above, two schools of thoughts emerge one approach is
propounded by Professor Cohen-Jehoram, he explains the manner how law regulates
information with three concentric circles ( See picture-6.3).
Copy Rights Law
Media Law

Information Law
(Picture-6.3)
He believes that individual at the out set establishes copyrights over a subject matter
and then media law governs the dissemination of the same thirdly information law deals
with the production, processing and distribution of information as a whole not just
publicly disseminating information. In spite of the criticisms like this model failed in
mapping the legal treatment of information, it has not established a clear reason behind
positioning copyright law at the center or it does not explained the relation between
media and information law etc, this theory has established the genesis of information law
approach.
Professor Dommering propounds the second school of thought; he opines that the study of
information law is the study of the communication as a whole. To put his theory
diagrammatically (see Picture –6.4)
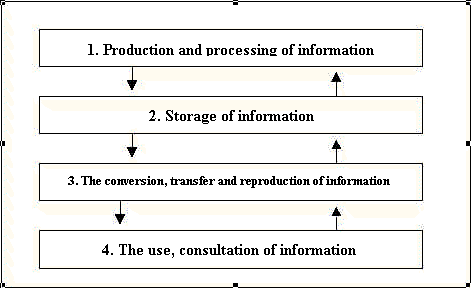
(Picture-6.4)
The Professor Dommering theory attracts the attention of legal scholars because his
theory splits information technology in to communication processes whereby facilitating
regulation of each segment of information communication. The beauty of this theory is,
every law like copyrights, media and communication so on and so forth have their own
respect fields of operation and no single law has occupied center position. Professor
Dommering’s theory broadens the scope of Information technology laws. And clear
demarcation of communication regulations can also be seen. If Indian technology law adopts
this approach perhaps the Indian Communications Convergence Bill should be passed. Because
this bill unifies all communication systems, and brings all of them under one regulatory
body.
Property – cyber space:
‘Proprietary ship’ an age-old concept of mankind, has always been brought to
discussion, whenever threat to its existence has come. All the time man tried his best to
protect his proprietary ship over the things he has access.
This terms is used in dissimilar ways by many schools of thoughts,
- In its widest sense, includes all the legal rights of a person of whatever
description.
- It includes proprietary rights of a person and not his personal rights
- In other sense, the term property includes only those rights, which are both proprietary
and real.
- It includes only corporal rights or rights of ownership in material things.
- It includes greatest rights of enjoyment (Austin)
Though, many jurists tried define property, but nevertheless each definition has its
own contextual significance. When it is said that property includes all legal rights, they
certainly mean it and that perhaps suits to the then prevailing legal and social
conditions. But when the circumstances have changed they went in search more appropriate
definition. As is rightly pointed out by Erle J.: " The notion that nothing is
property which cannot be earmarked and recovered in detenu or trover, may be true in an
early stage of society when property is in its simplest form and the remedies for the
violation of it are also simple, but it is not true in a more civilized state when the
relations of life and the interests arising therefrom are complicated"
It seems in the wake of Information Technology the proprietary rights of interent users
are going to be a complex problem. Questions pertaining to tangibility, intangibility,
movability and immovability of cyber property and can web page be sold, leased,
transferred, bequeathed, is total alienation is possible or not? So on and so forth are
going to occupy center points of ‘cyber prosperity jurisprudence’
But by using cyberspace as a metaphor we can resolve most of the problems of cyber
proprietary ship. The metaphor universally accepted with regard to property is
‘property is bundle of rights’ and the central tenet of property jurisprudence
is that, property is the legal right to exclude others. To put it more clearly, property
rights in the internet are negative rights, they lay what is not jurisdiction rather what
is jurisdiction. In other words as long as a computer does not violates the rights of
others such computer is said to have been within its jurisdiction. This refers that
wherever a computer interacts with other computer transgressing its property lines there
and then such computer is said to have violated the legal rights of the others. Therefore
it is the violation of legal rights of other that will mark boundaries for proper use.
The primary question that needs to be answered is whether website constitutes
property or not? Though we do not have any legal pronouncement as on today directly
dealing with the nature of the websites, we can consider a website as property because, we
refer websites as ‘sites’ like any other physical place, and we use the terms
like ‘web traveling’, ‘visiting’ etc which in turn establish most of
the features of physical properties.
Interestingly the trespass against chattels has also found place in
cyber space. In the case of ebay vs Bidder’s edge court emphasized on chattel
trespass. In the case of State v. McGraw court held that misappropriation of computer
resources could constitute trespass against chattel. In another casethe suit is one for
defamation claim under the common law, as well as one for unauthorized accessing of
e-mails from the personal e-mail account of the plaintiff. Which is challenged as
unauthorized intrusion in the personal domain of the plaintiff. The court held that an
email account would constitute a requisite place. The court held that as per The
Electronic Communications Storage Act, Section 2701 "it is violation for anyone who
intentionally accesses without authorization a facility through which an electronic
communication service is provided and thereby obtains, alters or prevents authorized
access to a wire or electronic communication while it is in electronic storage in such a
system". Court observed that the electronic mail stored on Microsoft’s server is
with in the definition of electronic storage.
With this case it is clear that electronic mail stored on
Microsoft’s server constitutes property, and invasion of it would constitute
violation of rights.
It is clear from the above facts that, well (pre) defined principles of property are
applied in cyberspace. But, interestingly the cyber property rights and traditional
property rights should not be viewed on same parlance. It seems that the judiciary intends
to fit this abstract space in to strict jackets of traditional property principles. To
quote one basic reason, cyber space is not a physical space and clear demarcation of
public domain and private domain is impracticable which requires lot of judicial maturity.
Cyber invasion:
We understood sociological perspective of cyber space invasion, but the
legal consequences of such invasion are some thing different. Some body invaded cyber
space to disseminate knowledge, to inform, to facilitate, to govern, to serve etc and the
others have invaded cyberspace to unshackle the foundations of most (presumably) secured
nations, to hack information stored in a remote computer, to destroy, copy documents kept
in a computer, to defraud and to bring financial crisis in the country etc., enlisting the
reasons for invasion and kinds of invasions would defeat the ends of our discussion.
According to statistics provided, in the year 2002, 625 million were accessing web sites
on the internet; the current estimates may cross 700 million by the end of 2003. So any
useful services provided on internet would facilitate nearly 700 million people perhaps no
human could physically reach these many people in his lifetime as is rightly pointed out
by James Madison " Knowledge will forever govern ignorance, and a people who mean
to be their own governors, must arm themselves with the power that knowledge gives. A
popular government without popular information or the means of acquiring it, is but a
prologue to a farce or a tragedy or perhaps both". But if we look the amount of
crime growth, the complaints filed in 2002 are 1,351,897 (3,704 per day) and Complaints
filed in the year 2001 are 701,939 (1,923 per day) it clearly indicates that using
computer is plugging to liability itself.
Malicious invasion:
Broadly speaking there are two kinds of malicious invasions one is
technical and other is non-technical invasions- the examples for technical invasion are
destruction of digital information through use of viruses, trojan horses, cyber punks,
phakers etc which requires technical know-how. Secondly non-technical invasion, for
example some hackers enjoy cracking systems. They do not intend to commit any further
crime. This is debatable whether such invasion constitutes crime or not, in its strict
sense this kind of invasion may be considered as trespass.
According to the recent statistical estimates the malicious invasions
over cyber space are:
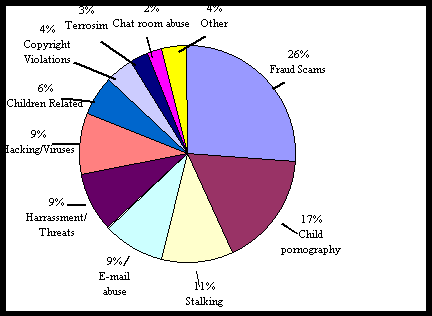
This kind of enormous increase of cyber crimes are reported in the
countries like U.S where as in India though crimes are not reported, they are being
committed and the consequent results are going un noticed. Before situation goes out of
our hands better we get ready with all possible remedies.
Cyber Scandalous:
Business Opportunities scam:
This scam talks about easy earnings and claims that this business requires
no selling, buying, meeting people on fields. They come with an idea of making money
through internet business. Most of the internet users are familiar with this kind of mails
but surprisingly if any one indulges in this kind of business perhaps he can never
recover.
Bulk email scam:
Bulk e-mail scandal offers thousands of e-mail address on payment of some money or they
offer services to send mail to thousands of addresses charging some amount for the same,
most of the business people would do this with an intention to reach out individuals but
they forget that selling or buying ones e-mail address without taking his consent is
crime.
Chain Letters Scam:
In this scam, the recipient of e-mail will be asked to replace his name against a name
appearing in the list of names by paying very meager amount of rupees and advises to
forward it to some body though bulk of e mails. To a common man perhaps this may not be a
difficult to pay meager amounts but ultimately after passing of some time one would find
that thousands of rupees are accumulated out of such mail and thousands lf e mail
addresses are attached to the mail and any good business man could make money out of this
resource.
Work at home scam:
You receive a mail that promises constant income flow without putting much effort. It
asks us is to follow the instructions sent through mail from time to time. Initially it
works well, we feel comfortable in working with that. But after some time it asks us to
deposit some amount to continue with them further, we be automatically inclined to deposit
amounts as soon as they receive deposits they stop functioning. And you don’t receive
any reply or e-mail from them further.
Health and diet scam:
Pills that let you lose weight, the exercises that let you appear smart, slim, health
and it offers herbal formula that liquefy our fat cells, in reality these gimmicks do not
work and no email can change our fat or fate. We may even receive case record of cured
customers to authenticate the information if we do not exercise our discretion
intelligently we may do away with loses.
Effort less income:
Hurry………….. lots of money waiting for you, we will send 5 lakhs if
you send 5/-…………. don’t miss it
……………..this is world’s best easy money making policy
recognized and approved by government………….. If these systems worked,
would not every body be using them? We need to possess cyber sense than cyber law.
Free Goods:
Some e-mail messages offer valuable goods like computers, other electronic items for a
very scanty amount, provided we join in a club and we are also asked to pay some amount to
join the club. Subsequently they ask us to introduce few more friends to the club so that
we could get the item free of cost. This kind of business has become very common in the
cyber world. They will certainly collapse leaving the poor customer with bare hands.
Investment Opportunities:
Scammer promises outrageously high rates of returns to our investment, with no risk.
Generally initial investors receive some applauding electronic letters and keeps them
under impression that scammer is spending their amounts in a proper way. But after
accumulation of some amount all of sudden scammer shuts down all his services and we
receive no response.
Cable Discrambler kits:
We will be offered through email or though a popping advertisement to buy a kit to
assemble a cable discrambler with which you can watch cable television without paying fee
for cable operator. But ultimately after all your efforts the devise that we have built
probably won’t work.
Vacation pricing promotions:
Some times we receive electronic certificates congratulating us for winning fabulous
prices, of free trip to Switzerland…etc. all these are vacation pricing promotion
scams, we should not get exited with this kind of mails instead we should be more alert.
Automatic Debit Scams:
Automatic debiting of our checking account can be a legitimate payment method; but
fraudulent people are abusing the system. We either get a postcard or a telephone call or
e-mail saying you won a free prize or can qualify for a major credit card: if we respond
to the offer, the telemarketer or webmarketer often asks you right away," Do you have
a checking account?" if you say " yes", the telemarketer/webmarketer then
goes on to explain the offer. The telemarketer/webmarketer may ask us to type number
printed at the bottom of our credit card. Once a telemarketer or webmarketer has your
financial information obviously we are inviting troubles.
Credit repair scam:
Credit repair scams offer to wipe out accurate negative information
from your credit file so you can qualify for a credit card, auto loan, home mortgage, or a
job. If we follow their advice by lying on a loan or credit application, misrepresenting
our Staff Number from Banks, PAN number from the Revenue Service under false pretenses, we
will be committing fraud.
Education and degree scams
Some time we receive mails inviting us to go for higher education. Scam schools often
use names that resemble those of legitimate colleges and universities. These schools does
not identifying information, a physical address, or contact information other than a toll
–free telephone number, they describe the traditional education with negative
phrases, most surprisingly the period of completing the degree offered would be 25 days.
This clearly indicates that we need cyber culture and sense to work in cyber space.
There are many number of scams that are identified in the internet they
are
- Internet Auction Fraud
- Internet Service Provider Scams
- Internet Web Site Design/Promotions - Web Cramming
- Internet Information and Adult Services - Credit Card Cramming
The list of scams enlisted above is not exhaustive rather it is illustrative. It is
argued that cyber crimes are distinct from physical crimes. But there is a common thing,
which is flowing under all crimes no matter whether they are committed in the cyber space
or physical space i.e. every time criminal is more intelligent than the victim added to
that, innovative Technology also brought to the use by criminals than by the governments.
Above all the legal implications involved to the contracts entered through e mail is
enhanced in the case of Shattulk v. Klotzbachit was held that e mail creates contracts
binding on the parties who use it. Both buyer and seller should be careful while
corresponding with each other through e mail.
What can be done to curtail these scams?
- Never give your credit card account number, bank account information, or Citizenship
Number over the telephone or Internet unless you are familiar with the company and know
why the information is necessary.
- Don't be afraid to ask questions even while transacting electronically.
- Companies do not ask for your bank account information unless you have expressly agreed
to this payment method.
- Legitimate lenders never ask you to pay for processing your application.
- If you don't have the offer in hand or confirmed in writing and you are asked to pay,
don't do it. It's fraud and it's against the law.
- Though we don’t have Better Business Bureaus (BBB) as like in US to report this
kind of mal practices we can as well Consumer protection agency.
- Don't reply to mail that you didn't solicit.
- Don't send money to lotteries that you don't know as genuine.
- Don't sign on anything.
For a positive upshot of ‘cyber jurisprudence’ in its space,
it demands for ‘Real knowledge’ about virtual space at the individual level,
‘Consensual knowledge’ at the level of institution and ‘Doctrinal
knowledge’ at the judicature level so that crystallization of cyberspace would be
possible.
Real knowledge – virtual space:
The term real knowledge signifies realistic knowledge which is more
practicable in cyber space because, thin line demarcates fact from fiction and more so in
cyberspace. William Gibson, author of "Neuromancer," published by Phantasia
Press early in 1986.
Gibson writes about fast increasing use of Cyberspace as, "a
consensual hallucination experienced daily by billions of legitimate operators, in every
nation, by children being taught mathematical concepts…A graphic representation of
data abstracted from the banks of every computer in the human system. Unthinkable
complexity. Lines of light ranged in the non-space of the mind, clusters and
constellations of data. Like city lights, receding…
This indicates that almost all activities that we do in physical space
can be done in cyberspace with all its decency, intimacy and accuracy. There are as many
experiences of cyberspace as there are perceptions of real place. Cyber space has become
intensely social. Two, considerably, recent litigations over two federal statutes
regulating sexually explicit content on the Internet has resulted in solid judicial
characterizations of cyberspace which are, Reno, Attorney General of the United States, et
al. v. American Civil Liberties Union et al, and the other case is American Civil
Liberties Union, et at v. JANET RENO, While addressing the importance of the cyber space
and internet, it was said that "the internet is a giant network that interconnects
innumerable smaller groups of linked computer networks: a network of networks… the
nature of the internet is such that it is very difficult, if not impossible, to determine
its size at a given moment.…the content on the internet is as diverse as human
thought, ….".
In the case of EBAY, INC., vs BIDDER’S Edge, INC the realistic
approach to the cyber offence is shown. In this case Plaintiff eBay, the court heard
Inc.’s motion for preliminary injunction on April 14, 2000. e Bay is an
internet-based, person-to-person trading site. E bay facilitates both buyers and sellers
to bid online. The users of the ebay site must register and agree to the ebay user
agreement. The agreement prohibits the use of " any robot, spider, other
automatic device or manual process to monitor or copy web pages or the content contained
therein without their prior expressed written permission".
Ebay currently has over 7 million registered users. Over 400,000 new
items are added to the site every day. Every minute, 600 bids are placed on almost 3
million items. Users currently perform, on average, 10 million searches per day.
A software robot is a computer programwhich operates across the
internet to perform searching, copying and retrieving functions on the web sites of
others. (Programs that recursively query other computers over the internet in order to
obtain a significant amount of information are referred to in the pleadings of various
names, including software robots, robots, spiders and web crawlers). A software robot is
capable of executing thousands of instructions per minute, far in excess of what a human
can accomplish. Robots consume the processing and storage resources of a system, making
that portion of the system’s capacity unavailable to the system owner or other users.
Consumption of sufficient place in any system would overload and makes processing of the
overall system slow. Ebay site employs "robot exclusion headers". To enable
computers to communicate with each other over the Internet, each is assigned a unique
Internet Protocol (IP) address. E bay identifies robotic activity on its site by
monitoring the number of incoming requests from each particular IP address.
BE is a company with 22 employees that was founded in 1997, it is more
like an information center which does not host auctions. When a user enters a search for a
particular item at BE, BE searches its database and generates a list of every item in the
database responsive to the search, organized by auction site closing date and opening date
etc. in early 1998, ebay gave BE permission to include information regarding ebay-hosted
auctions for Beanie Babies and Furbies in the BE database. Ebay wanted BE to conduct a
search of the ebay system only when the BE system was queried by a BE user. But the
relations were not gone well. Subsequently the method that BE systems adopted troubled
ebay therefrom ebay asked BE to stop posting their material in their web site which BE has
not turned up. It is argued by ebay that more than 100,000 robots a day to check the
prices of ebay which substantially brought down the speed of ebay systems.
If we look at the whole issue more technicalities are involved in
resolving it but interestingly court did not felt it complex instead it has applied simple
principle of "cattle trespass" and maintained that "where the conduct
complained of does not amount to a substantial interference with possession or the right
thereto, but consists of intermeddling with or use of or damages to the personal property,
the owner has a cause of action for trespass or case, and may recover only the actual
damages suffered by reason of the impairment of the property or the loss of its use".
It is also maintained that " unauthorized robot intruders into a
"brick and motar" store would be committing a trespass to real
property…….. similarly fundamental to the concept of ownership of personal
property is the right to exclude others…… the right to exclude others as one of
the most essential sticks in the bundle of rights that are commonly characterized as
property…" with the above observations court compared the robots with chattels
and unauthorized intrusion of robots in to the fields of others would amount to trespass.
And remedy is available in common law itself.
This kind of approach may give difficulties in the course of time but
till we understand and get clear picture of cyber space probably, the use of common law
principles is justified.
Consensual knowledge - Jurisdictional Paradigms:
The questions relating to jurisdiction in cyber space are complex
because the question how law should view the ‘cyber space’, should the cyber
space be taken as a place, a means of communication or a technological state of mind, is
itself debatable, in either case the reach of the space cannot be measured in terms of
length and breadth.
To put the questions of cyber jurisdiction more simply, let us assume
that Mr. X who resides in India, has purchased an online book offered by Mr. Y residing in
USA. How this transaction should be viewed shall we consider the issue as if Mr. X went to
USA or shall we treat it as if Mr. Y has come to India? What is the case if Mr. X
downloads the entire book through net? Would this make any difference with the previous
issue etc appears to be mere technical issues of jurisdiction but these questions have
some substantial jurisprudential significance, the quest to resolve would lead to the
crystallization of cyber space.
Traditionally the questions of jurisdiction are resolved under the
assumption that the mountains and trees will not change their place, but in cyber space
there are neither mountains nor trees. Every thing in cyber space is variable and nothing
is constant.
In a traditional contract, the jurisdiction is arrived at 1. The place
of defendant resides 2. Where the cause of action arose? etc. these parameters would not
work in cyberspace ( see above illustration). As a counter to this notion many jurists and
cyber law experts argue that, similar yardsticks of existing principles of jurisdiction of
physical space can resolve complications of jurisdiction of cyber space also. They
contend, jurisdictional matters in cyberspace are unnecessarily exaggerated and what ever
contract or transaction so entered through internet is taking place in one or the other
physical location, with physical seller and physical buyer and only difference between
ordinary transaction and this is the medium of communication which can not vitiate the
established principles. In the wake of this controversy, unless legislators as makers of
law, courts as executors of law have a common consensus and understanding about upcoming
of jurisdictional matters, it would not be possible to have a common rationale about cyber
jurisprudence and it would remain a dream to have sophisticated legislations.
Cyber space Doctrinaire!
Doctrines form part of jurisprudential study of any subject. There is a
dire need for the growth of doctrines in cyber law. Doctrines originate from the judicial
pronouncements. Legislation cannot create doctrine it can hardly recognize them. in
development of doctrines judicial pronouncements would do a lot. Doctrines are like
formulae in pure sciences, like (a + b)2 = a2+2ab+b2.
Similarly in case of Chemistry
H2+OÞ H2O. For
bringing out this mathematical and chemical formulae Scientists might have made
innumerable number of attempts on different combinations but once they are evolved, the
requirement for repeating all those combinations is not needed. For instance, to know end
result of the product of the sum of two variables, we simply substitute the variables in
the formula and resolve the problem which eventually reduces the labour and consumption of
time. Similarly, to apply a legal doctrine to a given instance would be like substitution
of facts into doctrine. For example: let us examine the following different instances:
- Mr. ‘A’, while driving his car at 90 km.p.h knocked down ‘B’ a
pedestrian, ‘B’ filed a case in Delhi High Court for compensation – court
gave its judgment in favor of ‘B’ asking ‘A’ to pay 50,000 Rs/- as
compensation.
- Mr. ‘X’, while driving his scooter at 60 km.p.h. knocked down ‘Y’ a
pedestrian, ‘Y’ went against ‘X’ to the Calcutta High Court seeking
compensation, court in this case resolved in favor of ‘Y’ and asked
‘X’ to pay compensation of worth Rs. 15,000/.
- Mr. ‘S’, while towing his moped at 5 km.p.h. knocked down ‘L’,
‘L’ went against ‘S’ to the High Court of Punjab seeking compensation,
court ruled in favor of ‘L’ and awarded him compensation of worth 1,00,000 Rs/.
If we analyze the given situations, all the cases are decided by
different courts in different times by different judges, against different parties,
different circumstances and different amounts of compensations, but still a common
philosophy can be expounded, that is " the quantum compensation in motor vehicle
accidents should be evaluated from point of the medical expenses and financial loss
sustained, irrespective of gigantic structure of the vehicle which caused injuries,
negligence of the driver and the speed of the vehicle at the time of meeting with
accident". In all these cases the arguments about the hugeness of the vehicle, speed
of the vehicle might have come but still the criterion adopted is financial loss and
physical damage.
If court happens to meet with similar situation, certainly court would
not be inclined to hear arguments on the points of hugeness and all but instead it just
asks the effected party to produce medical evidence and proof of financial loss he
sustained and decides accordingly. We have ‘n’ number of doctrines applied by
ordinary courts, but their application in cyberspace is debatable. For instance Lex
loci delicti, the doctrine of choice of law is taking its shapes in different issues
in the wake of information technology more particularly in case of internet defamation. In
Regie National des Usines Renault SA v Zhang [2002] Hight by a 6-1 majority (Callinan J.
dissenting) maintained that, double actionability choice of law test, which has its
genesis in Phillips v Eyreno longer has any place in Australian law. In farewelling that
test, Kirby J observed that it was ‘a rule inappropriate to a time of global and
regional dealings, technological advances that increase international conflictual
situations and attitudinal changes that rejects or at least reduce, xenophobic
(intolerant) opinions about the worth and applicability of the law of other
jurisdictions’. Though the adoption of inflexible lex loci delicti test simplified
Australian defamation law, it will not have such a significant effect on defamation
actions, where defamatory material is placed to the world audience in a web portal. as
court has to consider the defamation laws of each place in which the defamatory statements
have been placed, seen or read which is not practicable because defamatory laws are not
uniform in all countries. This again leads to the unification of internet defamation law
for which a common jurisprudential thought is needed.
In the Regan Gerard Gilmour v. Director of Public Prosecutions, it was
held while referring to Section 76C of the Crimes Act 1914, that a person commits an
offence under this section, if he lacks the authority to insert the particular information
into a computer, notwithstanding that he has general authority to insert other information
into such computer. It further held that an entry made without lawful excuse and known to
be false is said to have done that act without authority and is subject to punishment.
If we observe the above case the element of intention or motive with
which a person accessed the other’s computer has taken vital role in deciding the
guilt of such individual. If motive is good and exceeding the authority to access the
computer would not amount to crime but accessing computer with an intention to defraud
others may amount to crime.
But this analogy is reversed while convicting a person who is accused
of sending threatening e-mails, in spite of his plea that they were sent idly without any
intention to commit crime.
In the case of Norway v. Tvedt, the accused was the founder of a far
right group in Norway. He was convicted for posting racist material that mixed neo-Nazism,
racial hatred and religion, on a web site. The Asker and Baerum District Court in its
observation maintained that, "Tvedt made efforts to draw children and young people
into anti-semantic and racist beliefs". This judgment has become historic because it
is the first time someone in Norway has been sentenced to prison and Tvedt was convicted
for the contents of his home page, even though it was posted on a server that was based in
the United States and out of Norway’s Jurisdiction.
Computer is no more a mere window to the world of knowledge but it is
also like plugging to liability. In the case of Davis v. Gracey the 10th
Circuit held that computer equipment was more than merely a ‘container’ for the
files; it was an instrumentality of the crime". Therefore through this case the legal
status of a physical devise called computer has changed.
In the case of United States v. Thomas, Graphic Interchange Format
(GIF) file was not considered "intangible" for the purpose of federal obscenity
laws. If we analyze the above two cases, in one case computer is described as an
instrument of crime and in the other the tangibility and intangibility of computer files
were put to discussion which indicates that law is trying to influence every segment of
cyberspace. Though these cases are not sufficient in number to analyze the cyber
jurisprudence, yet I have tried to contribute some of my views to the evolving cyber
thought.
This kind of judicial expositions may bring about a permanent solution
to the cyber matters in the future course of time. I am not thrusting burden on judicature
to develop cyber jurisprudence exclusively but rather distributing equitably the risk on
legislation and on netizens.
Conclusion:
This conclusion may be to this article but certainly not to the
evolving cyber jurisprudence. I hope as is stated in the abstract, the ideas coined would
open new avenues for the crystallization of cyber space. It is not possible to cover all
the issues relating to this topic within the constrained paragraphs, with limited
phraseologies and with the availability of limited case law, I have ventured this because
it invites debate and attracts the attention of jurists. Hope my efforts will yield
fruits.
TOP
Print this Page Close this Window
 picture–2.1
picture–2.1

